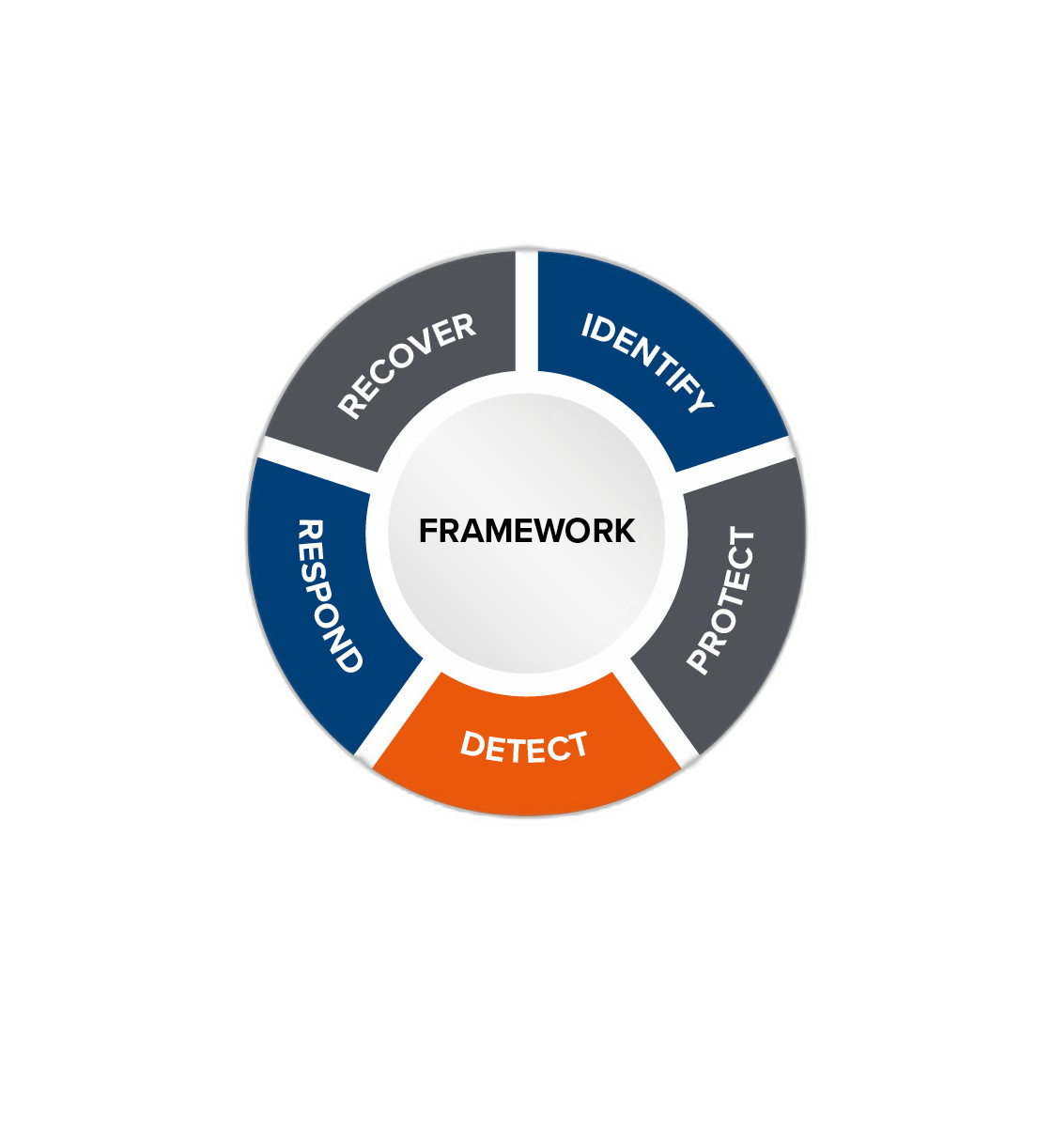
Protected: Risk Management in Cyber Security
There is no excerpt because this is a protected post.

There is no excerpt because this is a protected post.

Linux Configuration for starting off …
Continue readingLinux Configuration (DHCP and SSH) – CentOS Version

This is just an Introduction to setting up and attacking a standard Active Directory system …